Cybersecurity As A Service
Our advisory experts assist teams with cyber resilience and risk through managed security services using integrated strategies and cybersecurity excellence.
We have taken years of experience and turned it into solutions that protect client data, reduce operating costs, and inspire trust. Most importantly, we believe that data needs oversight with insight.
We are a team of information & security managers who watch over your business. We get to know your business priorities, deploy tools to protect your systems, administer your identity environment, and continuously monitor and evaluate the entire security program. In other words, we do cybersecurity assurance.
We at Data, Logistics & Security Solutions (DLSS) help prepare your business against the most advanced cyber adversaries and reduce your exposure to threats targeting applications, hardware (OT/IT), enterprise and infrastructure assets.
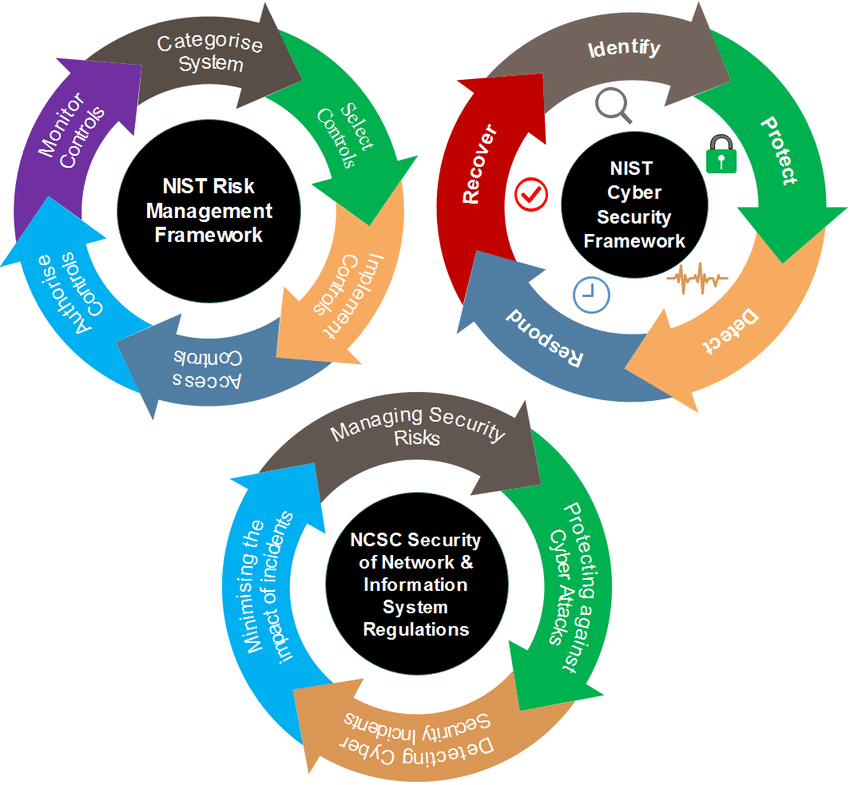
A holistic view of Cyber Security is essential to protect your business.
Our Cyber Security Wheel provides a comprehensive roadmap to guide your organization. We can help develop IT Security Policies, train staff, and ensure secure software and configurations.
NIST provides the Cybersecurity Framework (CSF) and Risk Management Framework (RMF) to guide organizations on securing their infrastructure, systems, and data.
We help build & manage cybersecurity programs by analyzing the maturity of your information security program, as well as identify gaps, weaknesses, and opportunities for improvement. With this, we can help lead your entire security/compliance/privacy strategy, to achieving a security accreditation (i.e. SOC 2, ISO 27001, CMMC, NIST 800 171, etc).
We have provided significant A&A support to various Theater Network Operations Centers (TNOCs) and Security Operation Centers (SOCs) in the USCENTCOM Area of Responsibility (AOR) including the U.S Army Central (USARCENT). Also, leading the transition of 13 geographically dispersed bases from DIACAP to the DoD Risk Management Framework (RMF).
AUTHORIZATION TO OPERATE (ATO) DOCUMENTATION
DLSS experts have the experience in policy & governance to help fast track clients in the ATO process, helping to write and implement authorization concepts in their earliest phases. Regardless of the complexity, our experienced teams of security engineers, and advisors, can help reduce accreditation timelines and better align security to development frameworks. If your security policies and controls aren't where they should be (we've all been there), we'll create new and improved ones to minimize your Cybersecurity risks.
federal risk and authorization management program (fedramp)
Our advisor and assessment services help organizations understand how their cloud offering aligns with FedRAMP requirements. We will assist your organization in preparing, achieiving or maintaining your cloud services for FedRAMP assessment and authorization. Our FedRAMP experts can lead you through the FedRAMP lifecycle and assist with identifying gaps, will perform a remediation plan, and provide architecture support to successfully achieve FedRAMP compliance and maintain continuous monitoring.
VIRTUAL CHIEF INFORMATION SECURITY OFFICER (VCISO)
vCISOs are outsourced security practitioners who provide remote Cybersecurity advisory services. With a vCISO, you'll experience all the benefits of a full-time CISO at only a fraction of the cost. As part of the vCISO offering we use our expertise to help organizations with developing strong IT policies / procedures and managing the implementation of their information security programs and compliance frameworks. With our vCISO services, your organization will have all the right tools to ensure success and a strong information security posture.
-
Security awareness training helps your employees stay informed about the Company's security practices. It is a formal process that seeks to improve employee security knowledge through education. Employee negligence or lack of knowledge often leads to security incidents and data breaches. Training plays a crucial role in the success of any cybersecurity program by reducing the human risk factor. Improve employee security awareness with user-tailored training. Starting at $1,000 USD monthly
Benefits of Security Training:
Develop a security-first work culture
Improve overall security awareness
Identify your team’s greatest areas of cyber risk
Prevent phishing and other social engineering attacks
Meet compliance requirements
Protect sensitive customer data
Some of the Topics Covered:
Reporting suspicious activity
Protecting your accounts
Passwords and passphrases
Password managers
Multi-factor authentication (MFA)
Social Engineering
Phishing
Patterns and tactics
Social media best practices
Reporting suspicious messages
Office security and remote work
Whiteboard hygiene
Clean desk best practices
Secure document handling and disposal
Remote work best practices
-
Cloud Service Providers (CSPs) interested in serving federal organizations must meet rigorous government-mandated security requirements as part of the Federal Risk and Authorization Management Program (FedRAMP).
Before a CSP can begin the FedRAMP certification process, they must first develop and implement FedRAMP-compliant documentation and controls. DLSS provides consulting services throughout the FedRAMP process and assists with Security Artifact Creation such as Security Assessment Plan (SAP), System Security Plan (SSP), Security Assessment Report (SAR), and Plan of Action and Milestone (POA&M) to get you prepared for your upcoming FedRAMP assessment and authorization.
We also provide the following as part of our consulting services:
Assist you to determine your cloud solution’s proper Federal Information Processing Standards (FIPS)-199 categorization of the risk level.
Conduct Vulnerability Assessment and Penetration Testing.
Conduct gap analysis to evaluating the sufficiency of security controls to determine organizations’ compliance level with FedRAMP requirements.
Evaluate, review and revise your Incident Response Plan, Process, and Procedures to ensure it sufficiently addresses FedRAMP requirements.